TL;DR
- Square root voting is a form of governance in which protocol participants vote in proportion to the square root of their tokens. For example, someone with one token casts one vote, and someone with twenty-five tokens casts five votes.
- This does a better job of balancing efficient governance and inclusive governance, as compared to the standard “one-token one-vote” model, where a few large tokenholders can dominate the protocol’s governance and ignore a broader community.
- Moreover, this also protects the rights of minority tokenholders and mitigates destructive attempts by the majority to expropriate their contributions. This is an active problem that many protocols currently face.
- However, to operationalize square root voting, the Sybil problem needs to be addressed — whether by identity, friction, or challenge solutions. There are several in development, and protocols must decide which ones are appropriate for them.
Introduction
Experimentation is rife throughout crypto — except in voting, where the standard “one-token one-vote” model is widespread. This model fits its traditional use case of public corporations well, but crypto is special. Unlike public corporations, crypto values decentralization, democracy, and community as intrinsic goals.
This blog post discusses an alternate form of voting: square root voting. Under square root voting, a protocol participant votes in proportion to the square root of her tokens. For example, a tokenholder with one token would get one vote, a tokenholder with sixteen tokens would get four votes, and so on. Square root voting is a variant of quadratic voting, which is often discussed as an alternative to the traditional “one-person one-vote” model in political democracies — but has made few inroads in crypto, beyond a few applications around quadratic payments.
For crypto, square root voting offers three independent and unique advantages.
- It strikes a balance between efficient and equitable communities, which better represents the ethos of crypto.
- It offers robustness against costly governance attacks, particularly by the majority on the minority. Indeed, crypto governance even lags corporate governance on this dimension, making reforms like square root voting overdue and necessary.
- It can be valuable for fair representation in two-tiered governance systems, which is vital as the field expands into more innovative and interconnected organizational structures.
Square root voting is not perfect. There are key operational challenges — especially the Sybil attack (i.e., one person creates multiple identities) — that must be addressed concurrently. However, there are many new mitigations to this attack, making square root voting more feasible than ever before. We believe it has earned a place on crypto’s long list of experiments.

Governance Goals: Efficiency and Equity
In crypto, an engaged and entrepreneurial community is paramount. But governing such a community entails tough tradeoffs, given the two competing goals of governance: efficiency and equity. Efficient governance generates the most value for participants, and it is the focus of traditional voting in corporations (and crypto). Equitable governance treats the opinions of all community members equally, and it is the focus of traditional voting in democracies.

- We call a governance system efficient if, when faced with a decision, it can maximize total expected value for its constituents (typically, expected monetary payoff, summed over all constituents) — regardless of the allocation among those constituents.
- We call a governance system equitable if, when faced with a decision, it treats the votes of all constituents equally — regardless of those constituents’ forecasts, preferences, tenures, funds, and backgrounds.
These goals don’t have to conflict, as efficient governance focuses on the outcome and equitable governance focuses on the process. But they conflict in practice.
To illustrate the tension, consider a simple scenario: an existing protocol, worth some $10 million in the treasury, is governed by a community (“the traditionalists”) holding the protocol’s 10 million voting tokens. A second community (“the radicals”) comes along and proposes some wild plan that they believe will increase the protocol’s value to $20 million. The traditionalists disagree — they think the radicals’ plan will make the protocol worthless.
Under traditional corporate and crypto governance, in which each token is worth one vote and is tradeable, there is an efficient solution. The radicals can buy the protocol’s tokens from the traditionalists at some price between $1 and $2, and subsequently enact their plan. From a monetary perspective, all parties — including the traditionalists — are better off. But by endowing tokens rather than people with votes, this governance process is not equitable. In this case, the traditionalists are sidelined from the protocol’s governance, even if they are more numerous than the radicals. In an extreme case, a single well-financed radical can buy out a protocol — and while the resulting outcome is perfectly efficient in terms of total value created, it also turns the governance process into a dictatorship.
On the other extreme, there is an equitable process, in which the radicals and traditionalists both vote, with one vote per person. But this will not deliver an efficient outcome, as one group will come away worse off from any vote, at least under their forecasts. Radicals can buy all the tokens they want, but their inputs are not treated differently in the final tally.
This fundamental tension stems from differing intensities of opinions. Some voting systems allow that intensity to be expressed without limitation to find the most efficient solution, and others deliberately ignore that intensity to treat all constituents equally. For example, mathematically, if one voter values a proposal at 2u and one values it at -u, then an efficient voting system would allow those valuations to factor directly into the final decision. By contrast, an equitable voting system would suppress those into simply a positive and negative vote, regardless of their sizes. But the choice need not be so stark: there might be a middle ground in which a voter can express the intensity of her preferences, but with some frictions.

Balancing Goals with Square Root Voting
Square root voting might strike that balance by picking a middle path, in which intensity — rather than being fully restricted or unrestricted — is moderated. Voters can acquire multiple tokens to express more bullish forecasts, but the effectiveness of that strategy diminishes as the opinion gets stronger. For example, a more passionate voter wanting to influence the vote by 10x needs to buy 100x the number of tokens — assuming we can stop voters from creating multiple identities (known as the Sybil attack, and discussed in a later section). In short, this system is partially efficient and partially equitable, and that balance makes it promising for crypto.
Consider the previous example, in which the radicals and traditionalists disagree. It is unclear whether square root voting ratifies the efficient or equitable outcome, but the tradeoff is clear. If preferences are intense, a minority can outvote a majority to deliver the efficient outcome through large and costly token purchases. If preferences are not particularly intense, the majority opinion will prevail, delivering an equitable outcome.
In theory, square root voting is not the only system that generates such a balance: any power function (with an exponent between 0 and 1) mapping tokens to votes does so. Exponents closer to one tilt the balance towards efficiency, and exponents closer to zero tilt the balance towards equity.
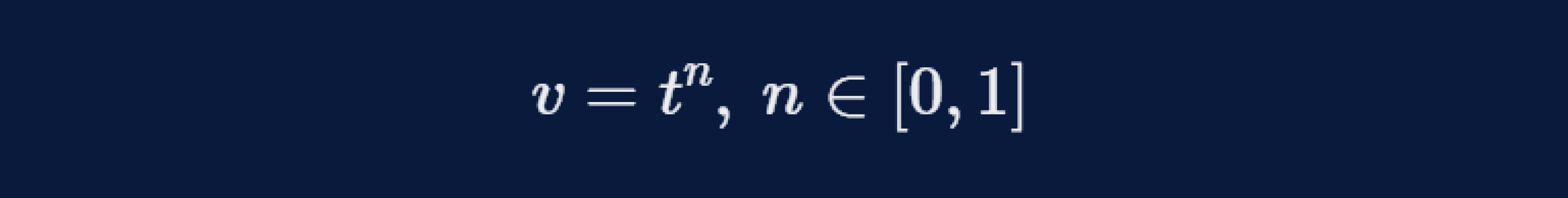
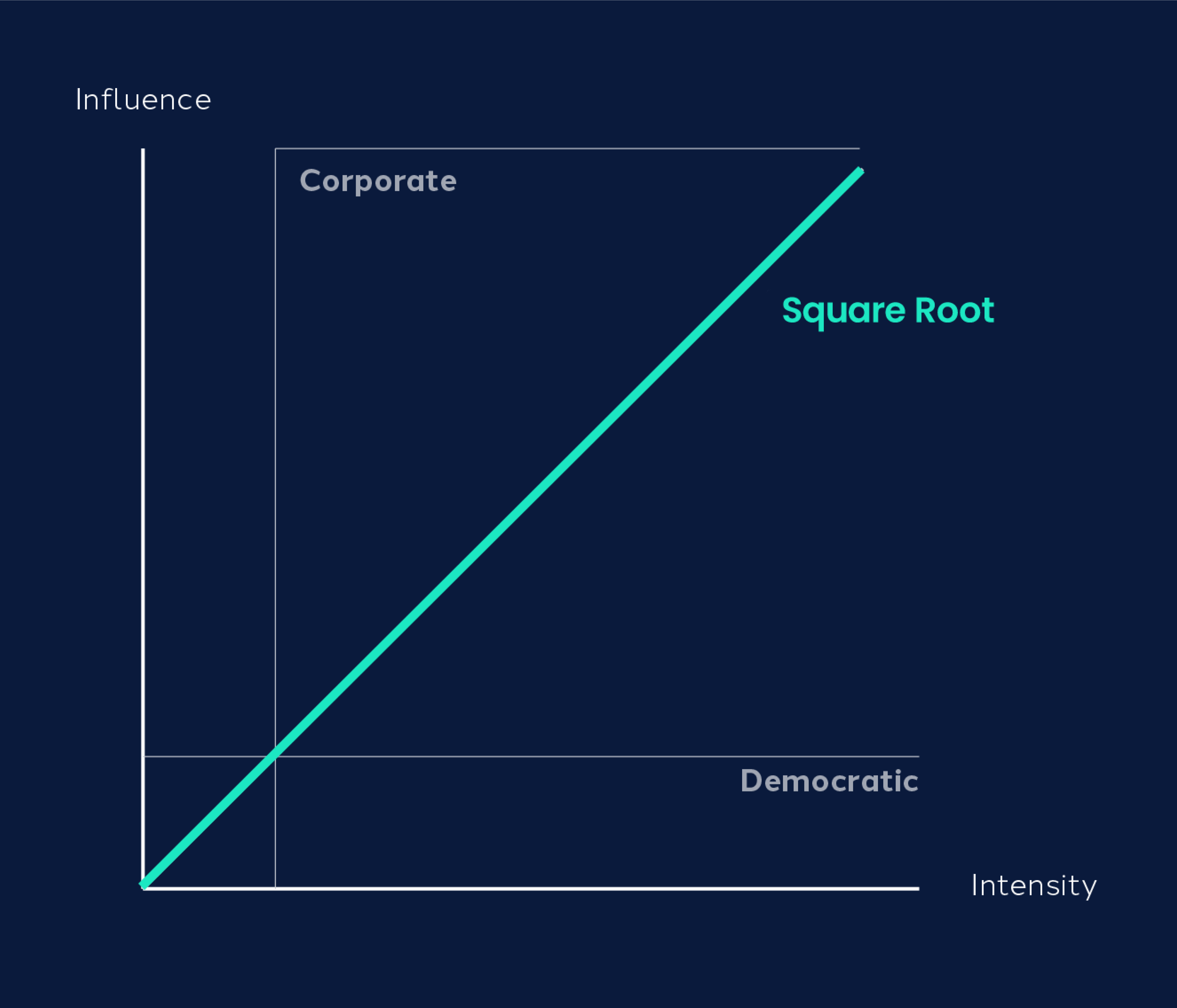
But square root voting has one elegant mathematical property, as demonstrated by Lalley and Weyl (2018) and visualized on Vitalik Buterin’s blog. In a simplified model, a rational voter’s influence is exactly proportional to the intensity of her preference. That is, under square root voting, a voter who is twice as passionate about an issue as her peer will influence the election twice as much (by purchasing four times as many votes). By contrast, under corporate voting, a voter who is twice as passionate will influence the election infinitely more (if sufficiently well-capitalized). Moreover, under democratic voting, all voters influence the election equally, regardless of passion.
A full proof can be found in the endnotes, but this can be depicted graphically as follows.[1]
Thus, square root voting offers one way to build more robust communities, which can be an enticing promise for systems trying to attract and retain constituents alike. Moreover, while square root voting is typically less efficient than traditional corporate voting and less equitable than traditional democratic voting, it can be better for a few aspects. We turn to these next, starting with enhanced efficiency in fighting governance attacks.

Defending against Destructive Governance Attacks
The traditional “one-token one-vote” model theoretically maximizes efficiency, but it has one weak spot. It is vulnerable to governance attacks, in which the majority tokenholders expropriate the value held by minority tokenholders. In the previous example, a disciplined and ruthless cohort of radicals could buy 50.01% of the protocol (paying between $5 million and $10 million for it) and then direct the protocol’s $10 million treasury back to them only. While expropriation isn’t technically inefficient (as a form of redistribution), in practice, it destroys value in three ways.
- Minority tokenholders often fight back, and that conflict can be intrinsically destructive.
- Minority tokenholders — conscious of this eventual risk — under-invest in the enterprise in the first place.
- Expropriative actions are widely seen as unfair and generate negative publicity for the protocol.
But square root voting checks majority power, making expropriation harder. More fundamentally, square root voting raises the Nakamoto coefficient for governance, making it harder for a small cabal of adversaries to seize control of the protocol. This generates many long-term benefits for the success of protocols.
To illustrate, consider the cautionary tale of Steem, as told by Decrypt. Crypto entrepreneur Justin Sun bought a 30% stake in Steem and planned to use that voting stake to integrate Steem with his blockchain Tron. However, the Steem community, using the powers of its executive council (known as witnesses), subsequently froze his stake. Sun then borrowed tokens from major exchanges, namely Huobi, to vote for his preferred witnesses to replace the incumbents, while the Steem community fought to keep their witnesses in place. The subsequent chaos was destructive for both sides, fracturing the Steem community and destroying Steem’s value.
We want to avoid taking sides in this story, but as a thought experiment: suppose Steem had utilized square root voting. What might have happened? We forecast two potential changes that would have improved the situation. First, the story’s very premise — a significant tokenholder trying to enact a vision not broadly shared by the community — would not have been possible, as those tokens would not have carried sufficient voting power. Relatedly, Sun’s second attempt to enact his vision, by borrowing tokens from major exchanges, would have been similarly ineffective. Second and more subtly, the opening salvo of the witnesses (freezing Sun’s tokens) might not have been possible. Witnesses on the Steem blockchain held considerable power, and one explanation for this design choice is that it acted as a check on the system. Square root voting is itself a check, and its presence could lower the need for costlier safeguards.
Steem is far from the only example. For instance, even before its ill-fated demise, three researchers published an analysis of various governance attack vectors for The DAO. These included vectors such as the “ambush attack” and “token raids” — many of which stemmed from last-minute surprise votes from a large tokenholder. As yet another example, Coindesk reported a governance attack involving flash loans, in which the BP Protocol borrowed MKR tokens to vote through its own proposal on the Maker DAO protocol. More generally, low participation in crypto voting allows even mid-sized actors to hold outsized influence and pass proposals that expropriate others.
Traditional corporate governance has long been aware of this risk, and so it includes supplemental legal protections for minority shareholders. For instance, the legal system prevents dilution of minority shareholders, requires supermajorities for particular decisions, forces high levels of information disclosure, and insists on a doctrine of fair treatment.[2] To see such protections in action, consider the case of Renren, which aspired to be the Facebook of China and listed shares (as ADRs) on the New York Stock Exchange in 2011. As Reuters reports, Renren was unsuccessful in its core mission but unrelatedly made lucrative venture capital investments. Renren’s CEO, Joseph Chen, then colluded with the firm’s other majority shareholders to extract those assets from Renren and thus cut out minority shareholders. Chen initially hid valuable information to depress the share price (hoping to execute a cheap buyout) and later attempted to transfer the best assets to a separate company that excluded minority shareholders. But such expropriation was not as easy as in crypto. Shareholders sued, and Renren’s settlement — while still being finalized — is estimated to be $330 million, which is even larger than the damages initially pleaded.[3]
Crypto governance is a step behind corporate governance, as such defenses are fewer and less established. Square root voting, which shrinks the relative power of the majority tokenholders, has a natural role in preventing expropriation relative to the crypto status quo. Such a governance system can prevent destructive tussles and bad PR, and encourage minority tokenholders to invest more freely in the protocol. This should make protocols more successful.
Square root voting does more than deter direct expropriation by a large tokenholder — it also deters indirect expropriation via a large tokenholder buying votes or bribing voters. Consider first vote-buying, i.e., the act of transferring a token from one party (the seller) to a second party (the buyer) for a short window during an election. The square root property immediately dissuades large buyers from harvesting votes from sellers. Interestingly, such a mechanism would also render unprofitable certain business models of pooling governance tokens, (e.g. Convex’s business model of directing Curve rewards), unless those protocols can keep accounts of underlying depositors distinct. Of course, the opposite dynamic is theoretically possible — sellers could sell their votes to lots of small buyers — but it is substantially harder for a diffuse group of small buyers to coordinate.
Consider second the act of bribery, in which the seller keeps the vote but votes per the buyer’s interests. While more feasible than vote-buying, it still requires buyers to bribe many small sellers to be effective, which is operationally complex and hard to keep secret.[4] This contrasts sharply with the traditional governance model in crypto, in which a few strategic buyers can interact with a few large sellers to buy or bribe votes secretly, and thus implement a governance attack. By forcing coordination across a large and diffuse set of agents, square root voting makes attacks harder to implement.

Enabling Equitable Two-Tiered Governance
At the other end of the spectrum, the traditional “one-person one-vote” model theoretically maximizes equity, with some caveats (e.g., young people, non-citizens, and felons). But in two-tiered governance systems, there is an even more subtle channel that disenfranchises voters. Square root voting plays a vital role in fixing that vulnerability and restoring fairness to such systems.
To illustrate the core problem, consider a hypothetical scenario: the three Scandinavian countries — Denmark, Norway, and Sweden — decide to form a federated political union, i.e., a Scandinavian Union. To keep the math simple, suppose Denmark and Norway have three voters, and Sweden has five voters.[5] How might they construct a governing executive body for the Scandinavian Union?
At first glance, proportional representation seems ideal. At the supranational level, the Swedish representative would get 5/3 the Danish and Norwegian representatives’ power, to compensate for each Swedish voter seemingly having 3/5 as much power in electing her preferred representative. But this logic, while qualitatively correct, is quantitatively incorrect. In fact, each Swedish voter has about 3/4 as much power as her Danish or Norwegian counterparts, which is approximately the square root of 3/5! This result is known as the Penrose square root law, in which a voter’s influence declines with the square root of her country’s population rather than linearly. A more detailed exposition is in the endnotes.[6]
Thus, an adjustment is needed at the supranational level to keep all voters equal: the Swedish representative should not get 5/3 as much power as the Danish and Norwegian representatives — but should instead get the square root of that number (~4/3).[7] This scenario illustrates the more general point: to ensure fairness, the upper tier of a two-tiered governance system should have voting weights proportional with the square root of their constituencies. Without such an adjustment, voters in large constituencies will have too much influence relative to voters in small constituencies.[8] While such a system does not exist in practice, there have been serious attempts to implement it — most notably the Jagiellonian Compromise, a proposal in which each country in the European Union would vote in proportion to the square root of its population.
But crypto might be well-poised to deliver the first implementation instead. On the surface, the industry appears far from utilizing it. Two-tiered governance systems do not exist, and protocols do not widely use the “one-person one-vote” model on that underpins any hypothetical lower tier. But the inherent innovation of the industry means that more complex and multi-layered forms of governance are coming. For instance, as crypto expands from financial applications to other digital communities, such as the virtual real estate of Decentraland and Axie, governance that looks more akin to that of political unions will be necessary. Square root voting should play a critical role in that shift.

The Sybil Attack
The Achilles heel for square root voting is the Sybil attack, i.e., a given person masquerading as multiple individuals. The Sybil attack can potentially be very effective at increasing voting power. For instance, an honest tokenholder with one hundred tokens could cast ten votes — or could be dishonest, create hundred independent accounts with one token each, and cast one hundred votes. Thus, the Sybil attack needs to be prevented to implement square root voting successfully.
There are three classes of solutions that could mitigate the attack. No class of solutions is perfect, but all show promise in mitigating the problem through different approaches.
- Identity solutions link accounts to people.
- Friction solutions make the Sybil attack costly to execute.
- Challenge solutions incentivize participants to police the protocol.
Consider first identity solutions, also known as “proof of personhood.” This can be implemented in a centralized manner, like allowlists or IDs, in which a single entity verifies accounts. But there are also decentralized takes on the same concept. For instance, Fred Ehrsam proposes a variant in which verified accounts get the full voting rights earned by their positions, while anonymous accounts get partial voting rights. Beyond that, in their review article of defenses against the Sybil attack, Siddarth et al (2020) discuss several fully-decentralized solutions. As one example, they review “pseudonym parties,” in which participants must show up virtually and demonstrate account ownership live to be verified, leveraging the fact that a person cannot claim multiple account ownership at a single point in time. As an alternative, they discuss decentralized “web of trust” solutions, in which others have to vouch for a given account holder directly or indirectly. Neither approach is perfect — the former can erode privacy without a careful design, and a small cabal of adversaries can game the latter — but both show promise.
Friction solutions are another alternative to make the Sybil attack costly to execute. For instance, in the short run, square root voting may work better on chains with high gas costs, because the cost of splitting funds to vote becomes substantially higher.[9] But relying on high gas costs seems like a strategy that is doomed to fail in the long run, as gas costs fall. Another variant uses a randomly-selected historical snapshot of account balances to record voters. If it is inconvenient to manage multiple accounts on a routine basis, this solution forces tokenholders to either represent their balances accurately or endure some permanent disutility. However, this may be inappropriate for high-turnover protocols, in which historical snapshots quickly become too outdated. Finally, reverse Turing Tests (e.g., CAPTCHA challenges) could stop a tokenholder from generating multiple accounts through bots. However, additional sophistication would be required to dissuade a large tokenholder from manually solving several dozen challenges, either directly or through platforms like Mechanical Turk.
Finally, challenge solutions can empower protocol participants to police themselves. In particular, consider a system in which a given tokenholder can accuse another tokenholder of creating multiple identities during an election, and both parties stake tokens on the outcome. After some investigation, the incorrect party forfeits tokens to the winning party. Logistically, this would require some investigatory work and an arbitration mechanism. Here at Jump Crypto, we’ve worked with the HUMAN protocol in the past, which develops infrastructure for hiring and compensating labor in a decentralized manner for such tasks. Such a protocol could provide the manual effort needed to underpin this or other Sybil-resistant systems.
Interestingly, while a minimum staking requirement is effective against Sybil attacks in general, it is harmful in the context of governance. Faced with such a requirement, a large tokenholder could not create too many identities, which is beneficial at first glance. However, small tokenholders below the minimum requirement would be excluded from voting altogether. Thus, this policy would allow only large tokenholders to vote. On the grounds of equity, this solution worsens the underlying issue.

Relationship to Quadratic Voting
Square root voting may appear related to quadratic voting, which was pioneered by Lalley and Weyl in 2012 and occasionally makes an appearance in mainstream publications. In fact, square root voting is just a specific variant of quadratic voting, that is more applicable to crypto governance.
In quadratic voting, individuals can vote multiple times for a proposal but pay the square of those votes. There are two ways to operationalize payments.
- A ballot might have multiple options, e.g., a civic election in which there are federal candidates, state candidates, local candidates, referendums, and so on. In this context, each voter is endowed with some total number of vote credits that she can spend across all options.
- A single-issue ballot might literally collect payment from voters, e.g., voting for a given candidate once costs $1, twice costs $4, and so on. In this context, the system retains the proceeds and distributes them to the entire community.
But neither variant is particularly palatable. The multi-issue ballot requires a voter to allocate and calculate summed squares, which can be tricky. The single-issue ballot is more straightforward, but it has not been popular since it involves an explicit monetary payment to vote.
Square root voting addresses both operational concerns: it is easy to explain to a voter, and it does not involve an explicit payment. At the same time, it retains all the core logic behind quadratic voting. In both cases, influencing the total election by one incremental unit incurs a cost that grows quadratically.
There are a few cases where traditional quadratic voting has been applied. For instance, in 2019, the Colorado Democratic Party used the multi-issue variant of quadratic voting to align priorities in the legislative chamber, by aggregating preferences and intensities. Moreover, multi-issue quadratic voting has been successfully replicated in other political contexts to identify the most pressing issues, e.g., the German Volt party and the 2019 and 2020 Taiwanese Presidential hackathons.
In crypto, quadratic voting has been applied in the context of grants. In particular, crypto has long sought a more decentralized way to allocate funding to nascent projects, particularly when the grants are substantial. Traditional methods, such as committee-based allocation, are too centralized; and simplistic methods, such as matching private contributions dollar-for-dollar, can be easily gamed. Given these constraints, Gitcoin Grants and Hackerlink have operationalized quadratic payments. Following the theoretical work of Buterin et al (2018), this mechanism directs public funding in proportion to the square of the sum of square roots of private contributions. As with any quadratic system, this incentivizes broad rather than concentrated support.[10] Such systems have also demonstrated innovation to handle adversarial attacks. Gitcoin Grants utilizes pairwise-bounded quadratic funding to dissuade collusion, and Hackerlink gives participants with a verified identity a boost in voting power to defend against the Sybil problem. Moreover, Gitcoin has announced that it is designing a protocol, called Aqueduct, to operationalize quadratic funding mechanisms for other ecosystem grant projects. Quadratic funding may yet become more widespread in crypto; and square root voting should join it.
Conclusion
Crypto communities are blends of financial and social organizations, and their governing structures should similarly represent blends. Square root voting offers one pathway, by balancing efficiency and inclusion. Moreover, square root voting can improve on existing governance systems: more efficient than the status quo by preventing governance attacks, and more inclusive in potential two-tiered governance systems. As long as the Sybil problem can be suitably addressed, square root voting can bring the theoretical promises of quadratic voting into reality.
Of course, in crypto, nothing goes off without a hitch. In practice, new challenges — from more subtle forms of collusion, misunderstandings by protocol participants, failed opportunities to ratify valuable proposals, and so on — will appear. But for too long, crypto has utilized the default governance model from the public corporation unquestioningly, despite its strongly differing ethos. Square root voting should earn its place in the chronicles of crypto, as the field constantly iterates and innovates forward.
Please let us know what we got wrong, as we'd like to understand this subject matter thoroughly and correctly. Thanks to the research team at Jump Crypto and especially to Jayant Krishnamurthy and Lucas Baker for feedback. This note does not constitute financial advice.
References
- Anonymous (December 18, 2021), "The mathematical method that could offer a fairer way to vote", The Economist.
- Baldwin, Richard, and Mika Widgren (June 15, 2007). "Poland's square-root-ness", VoxEU.
- Buterin, Vitalik (December 7, 2019), "Quadratic Payments: A Primer".
- Buterin, Vitalik (August 16, 2021), "Moving beyond coin voting governance".
- Buterin, Vitalik, Zoe Hitzig, and E Glen Weyl (2018), "Liberal Radicalism: A Flexible Design For Philanthropic Matching Fund", SSRN 3243656.
- Copeland, Tim (August 18, 2020), "Steem vs Tron: The rebellion against a cryptocurrency empire", Decrypt.
- Dolmetsch, Chris (December 9, 2021), "Renren's $300 Million Settlement Over SoFi Stake Is Rejected", Bloomberg.
- DoraHacks (November 3, 2021), "Dora Factory Community Grant-2 Voting Guide".
- Ehrsam, Fred (November 27, 2017), "Blockchain Governance: Programming Our Future".
- Foxley, William (October 29, 2020), "'Flash Loans' Have Made Their Way to Manipulating Protocol Elections", Coindesk.
- Gelman, Andrew, Jonathan Katz and Joseph Bafumi (2004), "Standard Voting Power Indexes Do Not Work: An Empirical Analysis", British Journal of Political Science, 34 (4): 657-674.
- Haig, Samuel (January 14, 2022), "Gitcoin revives debate over quadratic funding with new dev protocol", The Defiant.
- HUMAN, "Human Protocol Litepaper", version 1.3.
- Kelly, Liam (January 13, 2022), "DeFi Bribes Are on the Rise", Decrypt.
- Kirsch, Werner (2013), "On Penrose's Square-Root Law and Beyond", Power, Voting, and Voting Power: 30 Years After, pp. 365-387.
- Lalley, Steven, and E Glen Weyl (2018). "Quadratic Voting: How Mechanism Design Can Radicalize Democracy", American Economic Review: Papers & Proceedings, 108: 33-37.
- Mark, Dino, Vlad Zamfir, and Emin Gun Sirer (2016), "A Call for a Temporary Moratorium on 'The Dao'", unpublished whitepaper.
- Penrose, Lionel (1946), "The Elementary Statistics of Majority Voting", Journal of the Royal Statistical Society, Blackwell Publishing, 109 (1): 53-57.
- Posner, Eric, and Glen Weyl (2014), "Quadratic Voting as Efficient Corporate Governance", University of Chicago Law Review 81: 251-272.
- Rogers, Adam (April 16, 2019), "Colorado Tried a New Way to Vote: Make People Pay — Quadratically", Wired.
- Siddarth, Divya, Sergey Ivliev, Santiago Siri, and Paula Berman (2020), "Who Watches the Watchmen? A Review of Subjective Approaches for Sybil-resistance in Proof of Personhood Protocols", arXiv 2008.05300.
- Weiss, Kyle (October 4, 2021), "Gitcoin Grants - Quadratic Funding for the World".
- Zigelman, Michael, and Ivan Dolowich (Decembe 14, 2021), "Renren settlement highlights potential increased risk for corporate directors and D&O insurers", Reuters.
- Zyczkowki, Karol, and Wojciech Slomczynski (2004), "Voting in the European Union: The square root system of Penrose and a critical point", arXiv 0405396.
- To prove this, consider the following optimization problem, following Lalley and Weyl (2018). A protocol is holding an upcoming vote, and a representative voter is deciding how many tokens to acquire. She values the proposal at utility u, and each vote increases the probability of the proposal passing by a constant value p. Votes v are equal to tokens t raised to some power n. For simplicity, suppose each token also costs exactly n, which simplifies the math without changing the underlying proof. The voter thus must optimize v over the expression puv - nt. She finds the following solution for the optimal number of votes to cast, which are linked to the number of tokens to purchase through the protocol’s chosen voting system: (pu)^(n/(1-n)). To build intuition for this result, consider three cases. First, when n is equal to 0, the voter purchases one vote only, regardless of the proposal’s value to her. This is traditional democracy, in which each voter can vote once, regardless of their stake or intensity. Second, as n approaches 1, she purchases either an infinite number of votes for the proposal — assuming pu, i.e., the expected value of each vote, exceeds one — and purchases zero votes otherwise. This is traditional corporate voting, where unrestricted intensity of preferences can be expressed and the most passionate voter controls the outcome (assuming the voter has sufficient capital). Finally, when n is equal to 0.5, i.e. square root voting, v is exactly proportionate to pu. In particular, if the expected value of each vote doubles, the number of votes she purchases doubles (and the number of tokens quadruples). This exact proportionality is why square root voting is unique amongst all potential exponents between 0 and 1. ↩︎
- Interestingly, despite strong protections for minority shareholders in corporate settings, Posner and Weyl (2014) still propose square root voting (among other forms of quadratic voting) as one further defensive measure. ↩︎
- At this time, Bloomberg reports that the Renren settlement has stalled for two reasons: high legal fees to the plaintiff’s lawyers, and outsized compensation to current rather than former minority shareholders. However, the underlying outcome of the case does not seem at risk. ↩︎
- Of course, bribery can sometimes occur in the open rather than secretly, and square root voting is no more effective than regular governance in preventing that. As an older example, Vitalik Buterin points out this example in his blog. As a more recent example, projects like bribe.crv.finance are similarly creating explicit marketplaces for governance bribery, as documented by Decrypt. If such efforts become widespread, both traditional voting and square root voting may require other supplemental protections. ↩︎
- In reality, these stylized figures are highly accurate in relative terms: Denmark and Norway each have just under six million residents, and Sweden has just over ten million residents. ↩︎
- The Penrose square root law estimates the probability that a given voter is critical in determining an election, under the assumptions that every other voter has a 50% probability of voting yes and all votes are independent. If so, a voter’s influence declines with the square root of her country’s population, rather than linearly with her country’s population — because there are more voters (pushing down her influence) but more potential winning combinations of voters (mitigating that effect). Per the example by Baldwin and Widgren, consider “coalitions” of voters in small populations, to illustrate how (as the population grows), voters become less critical to coalitions but the number of winning coalitions rise. If there are three voters, a given voter A is critical in two coalitions {A, B} and {A, C} out of four winning coalitions — and she is not critical in {A, B, C} and {B, C} because changing her vote does not change the outcome. By similar logic, if there are five voters, a given voter A is critical in six of the possible sixteen ones. With these two competing effects, the probability that a given voter is decisive can be approximated, using Stirling’s formula, as a constant divided by the square root of the population. In this particular example, A is critical to 50% of the winning coalitions in a three-person system, and 37.5% in a five-person system. Her power in the five-person system is thus 75%, not 60%, of the three-person system; and 75% is indeed (approximately) the square root of 60%. ↩︎
- It is important to note that Penrose’s law is not without controversy, and one of its key assumptions — modeling voters as independent 50/50 Bernoulli draws — has been challenged. For instance, Kirsch (2013) models how voters could have correlated votes if there is sufficiently strong mutual information or mutual interaction. In addition, Gelman et al (2004) utilize empirical evidence to show that votes are not necessarily 50/50 draws. Both of these push towards conclusions that the upper tier of governance should have voting power closer to a linear function rather than a square root function of the underlying population, e.g., an exponent as high as 0.9. ↩︎
- Note that there are other solutions to moderate power, but they do not enjoy the nice mathematical symmetry of square root voting. For instance, the US government has a bicameral legislature, in which small states are well-represented in one chamber (the Senate), and large states are well-represented in the other chamber (the House). Alternatively, governments can change the threshold for ratifying policies, either to a lower or higher threshold, depending on the dynamics of the constituencies. ↩︎
- This argument assumes that funds cannot be held across multiple accounts indefinitely without some loss of utility. In some cases, this may be false, e.g., a protocol used for micropayments where each payment is lower than a typical account balance. In this case, an adversary could indefinitely hold multiple accounts, both for voting and transactional purposes. ↩︎
- To illustrate, consider two similar scenarios: in one, Alice and Bob donate $4 each to a project, and in the second, Alice donates $1 and Bob donates $9. In both cases, the public contribution — defined as the square of the sum of square roots — is $16. However, the first project earns that reward more efficiently (through $8, rather than $10, of private contributions) by having a broader and more equitable base of support. ↩︎
